Articles related to SASE ( Secure Access Service Edge) vs. SD-WAN (Software-Defined Wide Area Network) miss one point.
They usually explain just the technological difference between the two. However, what is also important is to know the purpose of both.
More specifically, what led to the creation of these technologies when MPLS and established security technologies were already mature and well-accepted?
A new term, SSE ( Security Service Edge), was coined recently, which is a subset of SASE, raising questions about the drivers that led to the creation of similar technology.
So we think the best way to explain SASE vs. SSE vs. SD-WAN is to explain them step by step in the order they were introduced, explaining what led to their creation.
Let’s start with SD-WAN first!
Why SD-WAN became popular? What problem does it solve?
SD-WAN became popular because of the increased use of SaaS applications and cloud-based apps by enterprises.
SaaS/cloud applications sit in the clouds, distributed everywhere. SD-WAN is transport agnostic and can use the internet as a transport medium, and as the internet is everywhere, it can connect to any destination easily and cost-effectively.
Let’s look at the example below.
In the earlier branch-to-HQ connectivity scenarios, MPLS was the primary transport technology.
This way of transport worked well as the DC at the HQ hosted all applications, so all the branch needed was a VPN to the HQ. As soon as the applications started moving outside the HQ because of the company’s move to SaaS and transition to cloud applications, this kind of transport became inefficient.
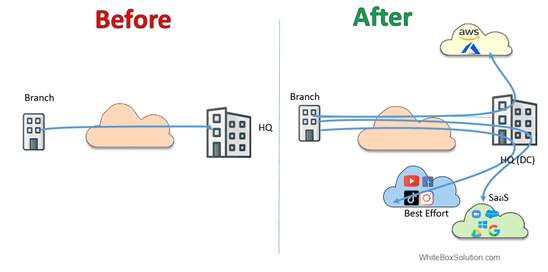 Fig. Enterprise connectivity before and after the SaaS.
Fig. Enterprise connectivity before and after the SaaS.
How?
Routing the traffic through the HQ meant a longer path to the destination, thus the additional cost of transport from HQ to the cloud and additionally more latency thus affecting the quality of service and application performance.
Can the traffic reach the cloud directly? everyone asked.
Perhaps a model like the following would help.
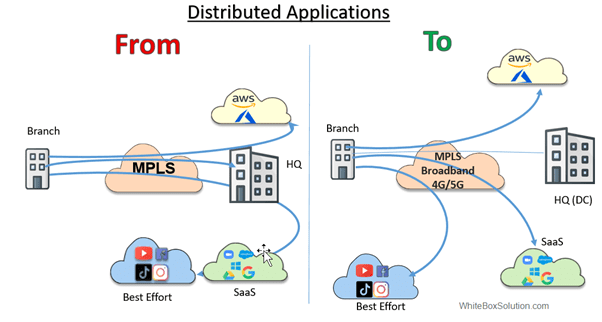 Fig. SaaS connectivity-before and after SD-WAN
Fig. SaaS connectivity-before and after SD-WAN
On the face of it, such kind of breakout to the SaaS is challenging. For one, security is a primary concern here. We may use broadband to reach the cloud, but the internet is insecure, isn’t it?
On the other hand, routing the traffic through the HQ has a definite advantage, as the HQ can act as a security gateway to the SaaS destination. So with appropriate security checks applied to the traffic at the HQ, traffic can be sent to the internet destination. This solves the security challenges, albeit additional cost of transport and latency.
Let’s see how SD-WAN solves this issue.
SD-WAN can seamlessly connect a branch site to the cloud bypassing the HQ with a secure tunnel.
SD-WAN requires placing an SD-WAN device at the branch site, which can connect to multiple SaaS destinations seamlessly using encrypted overlay tunnels. The good thing is that it can use any type of overlay, such as MPLS, broadband, 4G/5G, etc.
But here is another challenge with SD-WAN!
To provide foolproof security at the branch site, there needs to be additional security beyond encrypting the traffic. The branch is still part of the corporate network. The corporate security policies must be applied at every branch site beyond just the “encryption” the SD-WAN can provide.
More security checks are required to connect users with SaaS apps and private applications, like authorization authentication, in addition to the next-generation firewalls, URL filtering, etc.
Building an additional security layer at each branch site is expensive as it needs additional security appliances at every site. This is not only additional CAPEX but also OPEX.
This is where SASE can help.
How SASE solves SD-WAN challenges? SASE vs. SD-WAN!
SASE can provide an answer to security here:
SASE provides security through the cloud instead of premises.
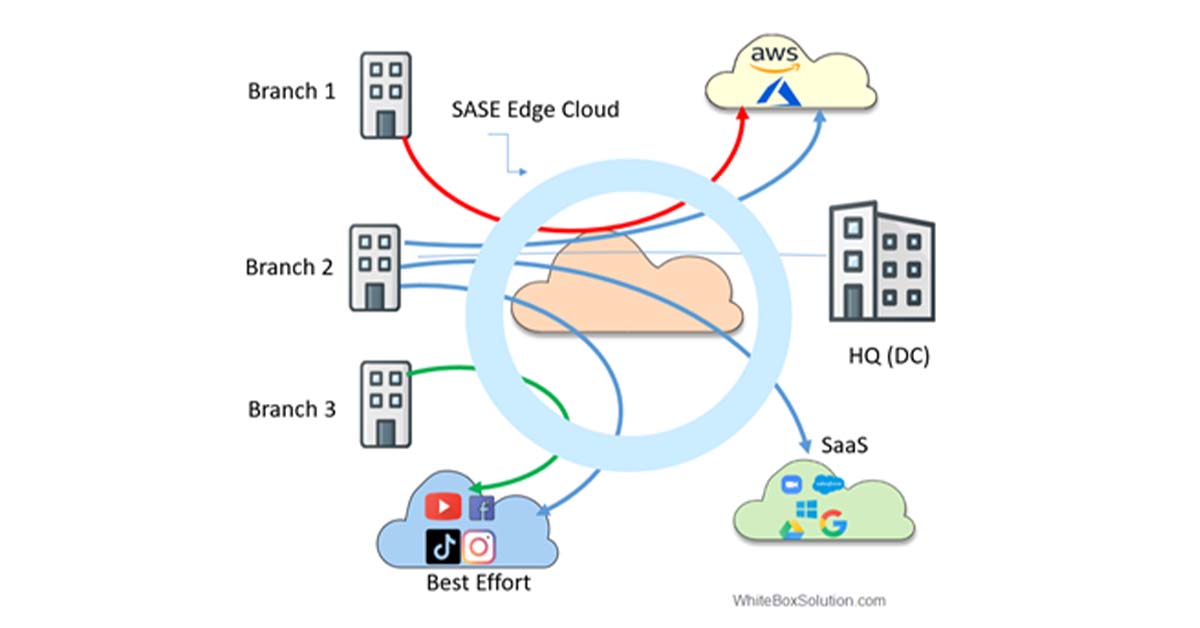
As the figure below shows, SASE establishes pops closer to the user, so security checks are applied closer to the user before sending the traffic to the appropriate destination.
Essentially, SASE includes the cloud-hosted security part and the WAN part( SD-WAN ) part. SASE is the evolution of security architectures today that are primarily based on security on-premises.
SD-WAN and security functions are closely integrated within the SASE solution. SD-WAN takes care of the networking part, while the cloud contributes to the security

SASE term was initially coined by Gartner back in 2019, and since then, it has become popular with many enterprises migrating their services to SASE-based architecture.
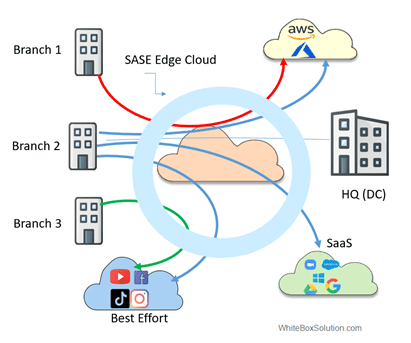 Fig. SASE Edge Cloud
Fig. SASE Edge Cloud
With SASE, WAN architecture is simplified as security management and security monitoring take place at the central location and in a unified way instead of sending the traffic to the HQ for security processing, eliminating the need for expensive backhaul.
Multiple components contribute to creating the security part of SASE, but some of them are the essential ones as below:
1.1 Zero Trust Network Access ( ZTNA)
ZTNA is the latest approach to security implementation. In contrast to VPN, which allows access to a LAN and hence everything that is part of that LAN, ZTNA “denies by default,” which means every user must have explicit rights to access services before it is allowed. This strategy, therefore, provides comprehensive access security for the enterprise. With SASE, ZTNA is implemented as part of the cloud rather than on-premises.
1.2 Secure Web Gateway ( SWG)
SWG protects a user from threats caused by user-initiated internet traffic through URL filtering, malicious code, and malware detection, thus ensuring that the user browses websites safely and his web-based traffic complies with corporate policy.
1.3 Cloud Access Security Broker ( CASB)
CASB sits in the middle between corporate users and cloud service providers, ensuring corporate security compliance in terms of authentication, authorization, malware detection/filtering, single sign-on, device profiling, logging, tokenization, etc.
1.4 Firewall as a Service ( FWaaS)
FWaaS is a cloud firewall that provides Layer 7/next generation firewall, enabling advanced security like IPS, URL filtering, DNS security, etc.
What is Security Service Edge (SSE)?
So far, so good; we have seen that SASE makes it possible to enable both security and networking, and in the evolution of a corporate to use distributed cloud services, SASE will play a central role.
However, here is a challenge for the SASE.
When Gartner introduced the original SASE concept, one of the driving points was that a single vendor SASE with (SD-WAN and security from the same vendor) would reduce the operational complexity and a recommended approach. However, with time, there was a realization that it is challenging to have a single vendor SASE considering there are two different sets of components, such as networking and security. While some vendors from networking backgrounds tried to evolve into the security space, another set evolved from the security space to the networking space so it was rare to find a unified SASE vendor.
There was also a challenge as the segment of buyers differs in an enterprise; if an enterprise adopted a a phased approach, such as buying SD-WAN first and buying SASE later, most likely, the buyers came from different departments.
The buyer for SD-WAN comes from the networking department, while the buyer for cloud security comes from the IT department. This would challenge who owns the unified SASE offering.
Last but not least, the COVID era and the post-period showed an increase in employee remote working, with remote workers needing to connect to the nearest cloud security gateway to use the enterprise SaaS, thus eliminating the need for SD-WAN.
Therefore wouldn’t it make sense to have a SASE offering without SD-WAN? This is precisely SSE or “Secure Service Edge,” a term introduced by Gartner in 2021.
Now, there is an independent Magic Quadrant for SSE ( Security Service Edge) by Gartner.
SSE provides security as a service in the cloud (access control, data security, threat protection), with the same components as SASE i.e., CASB, FWaaS, SWG, and ZTNA but without the SD-WAN component.

SASE vs. SSE
SSE is a subset of SASE, whereas SASE offers integrated and a unified service offering that includes cloud-hosted security ( such as ZTNA, SWG, CASB, FWaas) with a WAN networking layer such as SD-WAN to allow secure and optimized WAN connectivity between a user and applications, SSE only is the cloud-hosted security part of the SASE and can be offered independently by a service provider without a networking layer.
The following table summarizes the differences between SASE, SSE, and Networking.
| SASE Secure Access Service Edge |
SSE Security Service Edge |
SD-WAN Software-Defined WAN |
|
| Components | Cloud-hosted security + WAN networking | Cloud-hosted security | WAN networking |
| SD-WAN Software-Defined WAN |
|||
| ZTNA Zero Trust Network Access |
|||
| SWG Secure Web Gateway |
|||
| CASB Cloud Acces Security Broker |
|||
| FWaaS Firewall-as-a-Service |
About Lanner’s SD-WAN solutions
Lanner is a leading manufacturer of vCPE/UPE and white box platforms for purposes such as SD-WAN, NFV, SDN, Edge computing, and Open RAN.
It has a presence in the US through its subsidiary, Whitebox Solutions (www.whiteboxsolution.com).
LANNER vCPEs and uCPEs devices have pre-integrated major SD-WAN and VNF application providers. It can provide customized solutions for branch offices (small to medium offices) all the way up to big data centers, available in desktop and rack-mounted style forms.
You can visit Lanner’s SD-WAN solutions at
https://www.lannerinc.com/applications/sd-wan/pre-validated-ucpe-platforms-accelerating-your-sd-wan-deployment
References
https://www.gartner.com/en/information-technology/glossary/secure-web-gateway
https://www.gartner.com/en/information-technology/glossary/cloud-access-security-brokers-casbs
https://www.zscaler.com/resources/security-terms-glossary/what-is-firewall-as-a-service