

benefits including increased efficiency in operations and management for
distributed workforce. Even as many enterprises begin adopting cloud
computing processes, there are migration challenges including network
reliability, security, and availbility.
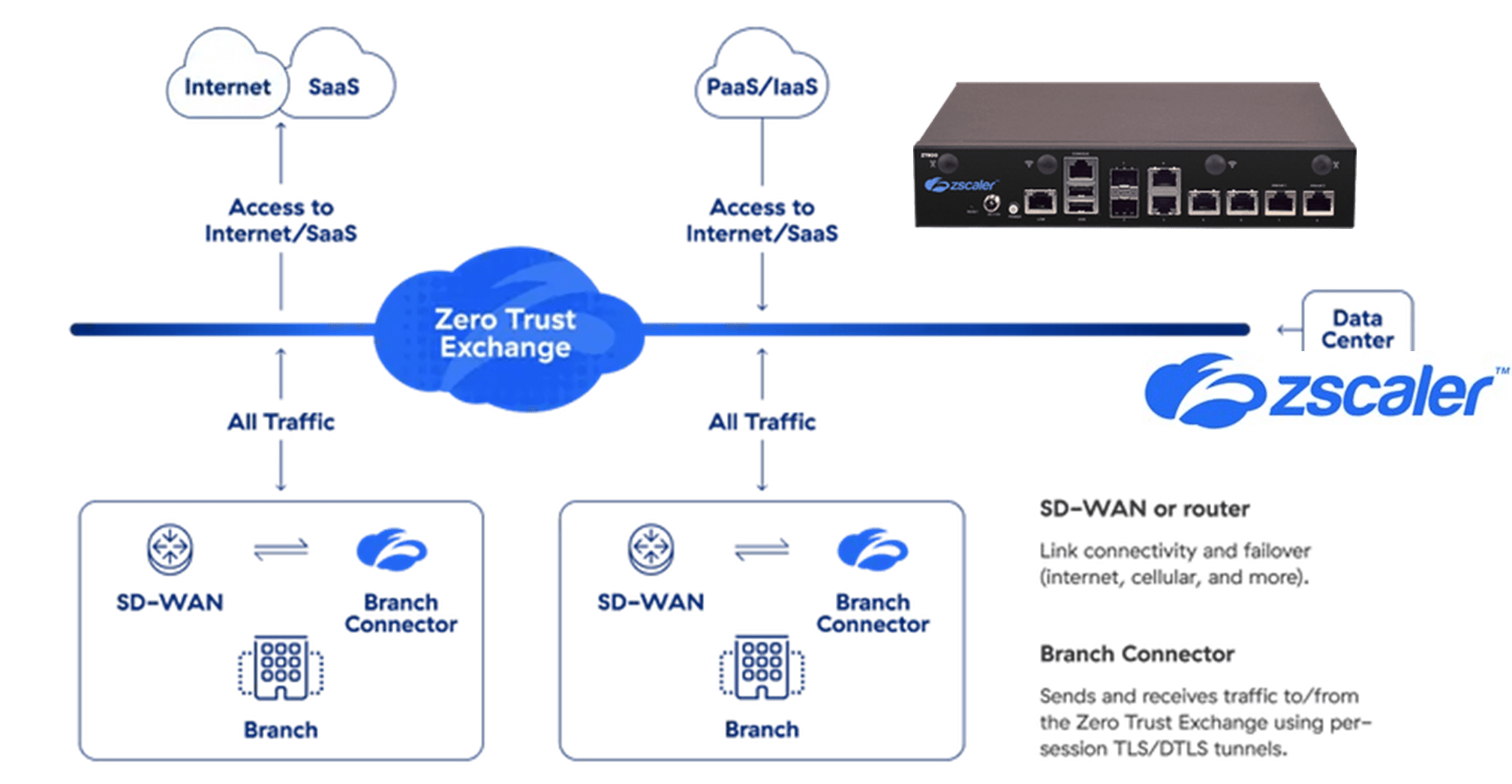
Lanner works with Zscaler to enable next-gen Zero Trust Branch Connectivity by
reducing cost, complexity and security risk. Lanner’s L-1515 uCPE platform
features Zscaler Zero Trust Exchange software that enables secure access for
users, workloads, and devices to the internet and multi-cloud applications
with zero trust connectivity
Lanner has a portfolio of uCPE devices supporting S-M-L-XL deployments
that range from Atom – Xeon performance.

Lanner uCPE L-1515 Product Features
-
Intel® Atom® C3000 Processor (Denverton) Max.
-
4x RJ45, 2x SFP & 2x RJ45 (By SKU)
-
2x 260-pinDDR4 2400/2133/1866MHz ECC/Non
-
ECC SODIMM (by SKU), Max. 64GB
-
Design ready for 5G Sub-6 and WiFi 6
-
1x RJ45 Console, 2x USB 2.0
-
2x Mini-PCIe, 1x M.2 2242 B Key, 2x Nano SIM for M.2
-
1x 2.5” Drive Bay (Optional)
-
Supports TPM 2.0
-
1 x Cooling Fan w/ Smart Fan (SKU A~E) or 2 x Cooling Fans w/ Smart Fan (SKU F)


Zscaler Zero Trust Exchange
Secure work-from-anywhere: Employees can safely and seamlessly work from anywhere without having to worry about the network or
whether or not they need to turn on a VPN.
Ensure a great user experience: By enabling you to understand the experience of every employee for every application, zero trust allows you to consistently deliver a great user experience.
Prevent cyberthreats: Enable full SSL decryption and cyberthreat protection, not just for users, but also for cloud workloads, servers, and SaaS app.
Simplify user and branch connectivity – Transform legacy hub-and-spoke networks by allowing branches that rely on expensive MPLS
links or connecting users over VPN links to enable secure direct connectivity over the internet to any destination, regardless of where the user connects.
Zero attack surface : Adversaries can’t attack what they can’t see, which is why the Zscaler architecture hides source identities by obfuscating
their IP addresses. Because Zscaler removes an attack vector that traditional offerings expose, it helps to prevent targeting.
Secure cloud connectivity: Workloads securely connect to other workloads using zero trust and machine learning instead of relying on extending a traditional site-to-site VPN to the cloud, and thus the same risks of lateral movement.
Data loss prevention: Inspects your traffic inline, encrypted or not, and ensures your SaaS and public cloud applications are secure, giving you the protection and visibility you need.
Sales & Support Enquiries
Ordering Information
| Zscaler Model | Whitebox MN | CPU | Core Count |
Memory | Storage | Others |
| ZT600 | L-1513E-4CL-16E-256M-ZS1 | Atom C3436L | 4 | 16GB | 256GB | TPM 2.0 |
| ZT800 | L-1515A-8C-32E-512M-ZS1 | Atom C3758 | 8 | 32GB | 512GB | TPM 2.0 |

